Overall Analysis: A Textbook “Pig-Butchering” Scam
This case follows a classic pig-butchering scam pattern. The scammer posed as a knowledgeable “teacher” or mentor, slowly building trust and emotional dependence (the fattening phase), before directing the victim to invest increasingly large sums into a fake trading platform. Once the funds were fully extracted, the scammer disappeared (the butchering phase).
Stage-by-Stage Breakdown
1. Trust Building & Setup (July 27–29, 2022)
What Happened
The scammer introduced himself as an experienced market expert. He said the market was “good right now” and encouraged me to learn crypto trading. He guided me through installing crypto apps, setting up wallets, and completing verification steps.

.He deliberately tried to dissuade me from using the computer and insisted that I use only my mobile phone. He taught me step by step through screenshots, guiding me “hand in hand”.
I was in a predicament because I was unfamiliar with how two-factor authentication (2FA) works. During this process, he kept pressuring me to provide my email address, name, and password.
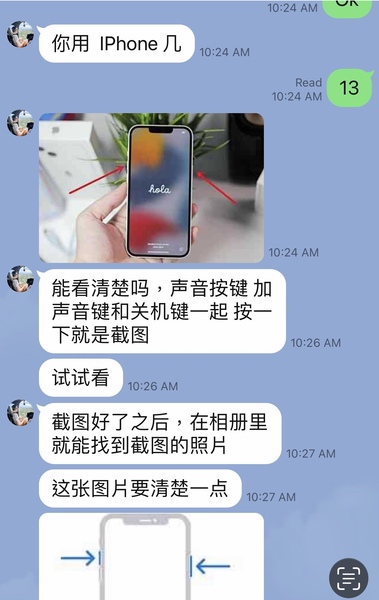
The scammer instructed me on how to obtain screenshots.
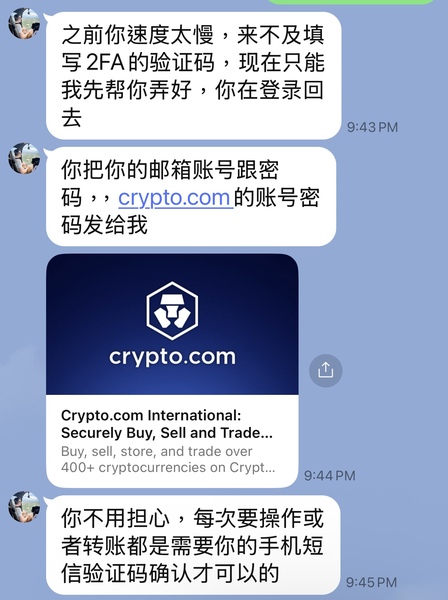
He put pressure on me, demanding that I provide my email address, name, and password after I failed 2FA authentication.
What This Really Was
• Authority & Urgency: Presenting himself as an expert created instant credibility and urgency.
• Control & Isolation: By steering me away from a computer and into mobile apps, he limited my ability to research or verify anything independently.
• Security Infiltration: His insistence on helping with passwords and 2FA was not assistance—it was account takeover. Once he had access to my accounts, he effectively controlled them.
This phase was about gaining trust and technical access, not investing.
The scammer taught me how to trade online.
2. Initial Investment & the Illusion of Profit (July 30 – August 2)
What Happened
As I struggled with authentication, I eventually gave him my email and password out of confusion and stress. He then moved funds from Coinbase into my wallet and introduced a trading website: keyburst.com, which displayed the KikiTrade logo.
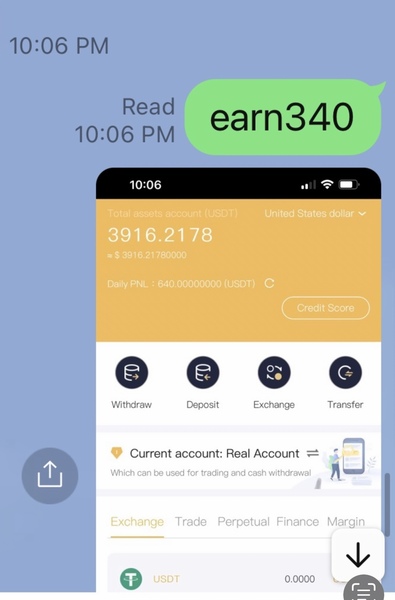
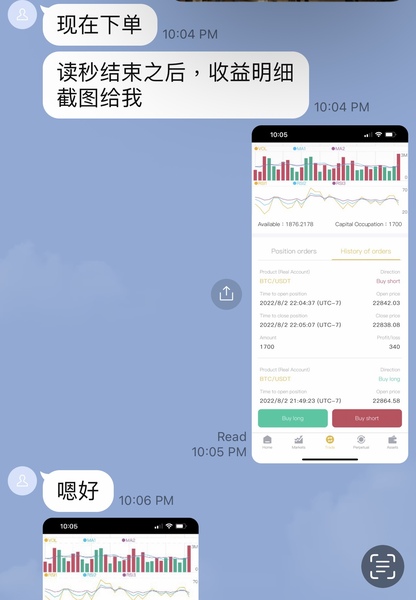
I was guided through small “trades” that appeared to generate fast profits—such as earning $300 in 30 seconds. He also showed screenshots of his own massive trades, claiming to earn hundreds of thousands of dollars.
What This Really Was
• Fake Platform: The website was a counterfeit version of a legitimate exchange. Even the logo was slightly different—a critical red flag.
• Fabricated Profits: The early “wins” were fake numbers designed to build confidence and trigger greed.
• Wealth Display: Showing extreme profits normalized the idea of risking large sums and made my investments feel small by comparison.
This stage existed solely to convince me that the system was real and profitable.

The fake Platform- KikiTrade.
3. Escalation & Large-Scale Fund Extraction (August 3–12)
What Happened
Once I believed the platform worked, the scammer escalated aggressively. He pushed me to raise tens of thousands of dollars, then hundreds of thousands. He instructed me to move IRA funds, wire money from my bank, and convert everything into cryptocurrency.
He guided every step: wire instructions, screenshots, talking points for bank staff, and explanations for delays. Funds were wired to Coinbase or Crypto.com, converted to Ethereum, transferred into my wallet, and then sent to “KikiTrade.”
In total, enormous sums—$41,500, $110,000, $200,000, and more—were moved under his direction.
What This Really Was
• False Justifications: Claims about “faster trades” or “avoiding holds” were lies to get money into crypto, where transfers are irreversible.
• Direct Theft: The wallet address used for “KikiTrade” was not a platform deposit address. It was the scammer’s personal wallet.
• Irreversible Transfers: Every time Ethereum was sent from my wallet to “KikiTrade,” it was permanently transferred to him.
At this point, the money was already gone—even though the fake platform still showed “trades” and “profits.”
4. The Final Butchering (August 13–26)
What Happened
While I was traveling, the scammer maintained casual contact—sharing trip photos and small talk—to maintain trust. At the same time, he orchestrated the most significant transfers yet.
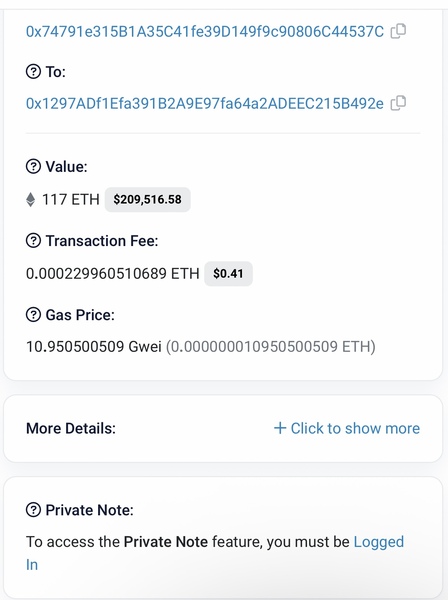
After purchasing Ethereum, the scammer instructed me to transfer from my wallet to KikiTrade, which is his wallet.
On August 22, he guided the transfer of 118 ETH, representing hundreds of thousands of dollars, directly into his wallet. He then staged another fake “trade” to make it appear the funds were still working.
After that, his only focus was pushing me to borrow money and raise additional funds, aiming to reach a total of $1.2 million.
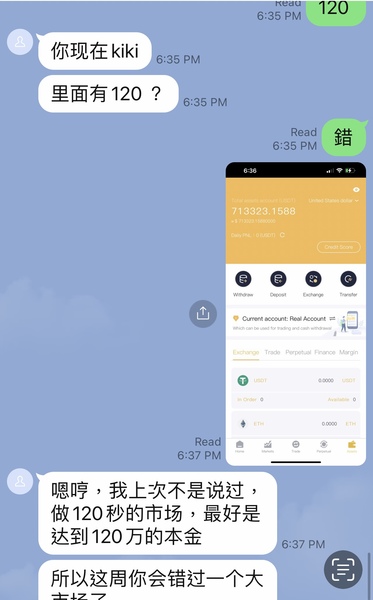
He kept urging me to borrow money and go into debt, with the target amount clearly set at 1.2 million US dollars.
What This Really Was
• Maintaining the Illusion: Friendly messages and staged trades were distractions while the theft was completed.
• Maximum Extraction: Even after draining nearly everything, he continued pushing for loans and debt.
• Pure Exploitation: There was no investment goal—only total financial destruction.
This was the peak of the fraud.
5. Ghosting & Exit (August 26 – October 2)
What Happened
Once my funds were exhausted, communication became sporadic. He made two calls on September 26 and sent a single message:
“Are you still alive?”
He left the chat permanently on October 2.
What This Really Was
• Final Viability Check: This message was not concerning—it was a last attempt to see whether I could still be exploited.
• Exit Strategy: Once he confirmed there was nothing left to take, he vanished.
• End of the Scam: This disappearance marks the definitive conclusion of the fraud.
Final Summary
1. Build trust and emotional dependence
2. Gain technical and financial access
3. Create fake profits on a fake platform
4. Drain all available assets
5. Disappear once extraction was complete




